Recently published
This page was published on [date_placeholder].
Recently updated
This page was updated on [date_placeholder]. See page history for details.
Purpose
This guidance has been produced in order to support Australia's medical device cyber security capability, embedding improved cyber security practices across the medical device sector.
This guidance on cyber security for medical devices is in line with existing regulatory requirements and will assist in supporting the implementation of risk-based regulatory approval pathways that are guided by and support the Australian Government's cyber security strategy- external site.
The purpose of this guidance is to help manufacturers and sponsors understand how we interpret regulations and thus indicate how to comply.
This is a guide only, and manufacturers and sponsors are encouraged to familiarise themselves with the legislative and regulatory requirements in Australia.
If necessary, seek professional advice as it is the responsibility of each manufacturer or sponsor to understand and comply with these requirements.
This document will evolve over time and updates and clarifications will be included as required. Feedback on the guidance is always welcome.
Alongside this guidance, we have produced medical device cyber security guidance for users.
About
The Australian government regularly provides updates and advisories on cybersecurity for Australian organisations at cyber.gov.au.
We recommend that medical device sponsors and manufacturers consult cyber.gov.au for the latest advice on various cybersecurity issues and education from Australian government.
It is noted that an advisory was issued in April 2022 for Australian organisations to urgently update their cybersecurity posture.
Connectivity and digitisation increase benefits and risks
Connectivity and digitisation of medical device technologies may help improve device functionality and benefit.
However, the connection of medical devices to networks or the internet exposes them to increased cyber threats that can potentially lead to increased risk of harm to patients.
These might include:
- denial of intended service or therapy
- alteration of device function to directly cause patient harm
- loss of privacy or alteration of personal health data.
Additionally, there are fundamental security interdependencies between medical devices and the networks they connect to.
Cyber security for medical devices must be considered as part of a layered, holistic security ecosystem. The cyber security landscape is constantly evolving.
Chapter 4 of the Therapeutic Goods Act 1989 (the Act) provides for the safety and satisfactory performance of medical devices, by setting out particular requirements for medical devices, establishing processes aimed at ensuring those requirements are met, and providing for enforcement of these requirements.
The requirements for medical devices include 15 'Essential Principles', set out in Schedule 1 of the Therapeutic Goods (Medical Devices) Regulations 2002 (the MD Regulations), which relate to the safety and performance characteristics of medical devices.
Assurance that relevant medical devices are appropriately cyber-secure is required for compliance with a number of the Essential Principles.
Lifespan of a medical device
Medical devices cannot generally be supplied in Australia unless they are included in the Australian Register of Therapeutic Goods (ARTG).
Inclusion in the ARTG requires considerations that span the life of a medical device, including:
- pre-market via conformity assessment
- market authorisation via inclusion in the ARTG
- post-market monitoring
- end-of-life / withdrawal of support.
Adopting a total product life cycle (TPLC) approach to risk and quality management is required.
Risk assessment and management
Assessment and management of cyber security risks that could compromise the health and safety of a patient, user or any other person, as with other risks for medical devices, is the responsibility of the manufacturer.
- Pre-market: Manufacturers are required to address cyber security risks during the design and development process. This includes:
- general considerations, such as the development approach; administration protocols; application of standards; risk management strategies; infrastructure, manufacturing and supply chain management; and provision of information for users
- technical considerations, such as cyber security penetration testing; modularised design architecture; operating platform security; emerging software; and Trusted access and content provision
- environmental considerations for the device's intended use, such as connecting to networks, and uploading or downloading data
- physical considerations, such as mechanical locks on devices and interfaces, physically securing networks, waste management (preventing capture of sensitive paper-based information)
- social considerations, such as designing out or minimising social-engineering threats (e.g., phishing, impersonation, baiting, tailgating).
- Post-market: Manufacturers and sponsors are required to continually assess and take action on medical device cyber security risk
- The cyber security threat landscape changes in short periods of time, therefore a compliant risk management strategy will demonstrate how medical device cybersecurity risk is reviewed and updated.
- Cyber security events that do not appear to immediately impact a medical device are still part of the cyber security threat landscape and will need to be considered as part of a compliant medical device cyber security risk management strategy.
Total product lifecycle guidance
The information provided in this section details the general responsibilities and requirements (for both pre and post-market consideration) for medical device manufacturers and sponsors to ensure that devices meet regulatory requirements associated with cyber security, specifically risk management frameworks, including:
- Medical device total product life cycle (TPLC) approach
- Medical device cyber security requirements under the Essential Principles
- Standards that may assist manufacturers and sponsors to meet the Essential Principles
- Proactive cyber security risk monitoring, and threat information and intelligence sharing.
Total product life cycle (TPLC)
Risk management is expected to be an ongoing activity, which is considered, controlled and documented across all phases in the life of a medical device, from the initial conception to development and testing, market authorisation, post-market use, and through to end-of-life and obsolescence.
Meeting these expectations is most readily achieved by adopting a total product life cycle (TPLC) approach to risk and quality management.
One standard that may be consulted to help with this is IEC 62304 (detailed in Relevant standards).
As with other risks, if cyber security risk is not effectively minimised or managed throughout the life of the device, it can lead to issues including: a medical device failing to deliver its therapeutic benefit, a breach in the confidentiality, integrity and availability of medical device data, or malicious unauthorised access to the medical device and the network it operates on.
Underpinning a TPLC approach is the ongoing application and updating of quality management systems including:
- risk management procedures
- change management procedures
- design procedures
- complaint management procedures.
As clinical use of a medical device is sometimes considerably longer than the expected lifespan of the technology that allows its operation (e.g. software and connectivity hardware), manufacturers and sponsors need to be aware of this challenge and work with users to effectively minimise risk.
Essential Principles
About the Essential Principles
For a medical device to be included in the ARTG, the manufacturer must demonstrate compliance with the Essential Principles.
The Essential Principles require that a manufacturer minimise the risks associated with the design, long-term safety and use of the device; this implicitly includes minimisation of cyber security risk.
Six general Essential Principles are relevant to all medical devices, and a further nine Essential Principles about design and construction apply to medical devices on a case-by-case basis, depending on the technology used within the device (refer to Therapeutic Goods (Medical Devices) Regulations 2002 - Schedule 1 for more information).
The Essential Principles are not a prescriptive list of requirements for manufacturers to comply with and instead provide high level principles for flexibility according to the characteristics of the device.
The legislation does not mandate the means by which a manufacturer must prove that they have met the Essential Principles.
It is a manufacturer's responsibility to determine which Essential Principles are relevant and to demonstrate compliance with these.
Compliance with the Essential Principles
A medical device must comply with the Essential Principles which set out the requirements relating to safety and performance.
We require that the Essential Principles are met by applying accepted best-practice regarding quality management systems and risk management frameworks, which is typically via application of state-of-the-art standards (See also Relevant standards).
Supplying medical devices that do not comply with the Essential Principles may have compliance and enforcement consequences; it may be an offence or may contravene a civil penalty provision of the Act1.
- the manufacturer is required to generate and maintain evidence regarding the quality management systems and risk management frameworks used to manage medical device cyber security to demonstrate compliance of the device(s) with the Essential Principles, regardless of the classification of the device
- the sponsor must have available sufficient information to substantiate compliance with the Essential Principles or have procedures in place with the manufacturer that will allow them to obtain such information and provide this information to us if requested.
The obligation to have information that demonstrates compliance with the Essential Principles lies with the manufacturer of the device.
However, the sponsor must be able to provide information to the TGA to demonstrate such compliance. This applies to all medical devices regardless of risk class.
Compliance throughout lifecycle
Throughout the medical device life cycle, manufacturers need to ensure continuing compliance with the Essential Principles.
Risk management for medical device cyber security requires assessment and corresponding action over the life-cycle of the device and with consideration of the multiple environmental factors that may be applicable.
Some considerations include that:
- Medical devices and associated networks they operate in can never be completely cyber secure, and that because of the share responsibility of cybersecurity, medical device users may represent a potential threat.
- Medical devices can be used by an attacker as a threat vector into their associated networks.
- The cyber security threat landscape is rapidly evolving and requires constant monitoring and appropriate corrective and preventative action from medical device manufacturers and sponsors, alongside cooperation or coordination with medical device users.
- Potential harm to patients and users from an adverse medical device cyber security event could clearly include physical harm (e.g. a device no longer operating as intended). There may also be other consequences for patients, users and the general community arising from a cyber security event related to a medical device, including for example, psychological harm, incorrect diagnosis, breaches of privacy through the disclosure of personal information, or financial consequences.
- Personal health data, including data collected from medical devices, presents a lucrative target for malicious activity, requiring secure storage and transmission solutions.
- Clinical use of the device is often considerably longer than the expected lifespan of the technology that allows its operation (e.g. software and connectivity hardware), and this technology often receives less frequent patches over time, or becomes officially unsupported.
Cyber security risks and the Essential Principles
As a cyber security risk can be a safety concern, consideration and minimisation of such risks are imperative to compliance with many of the Essential Principles.
In particular, Essential Principle 1(b) requires, among other things, that a medical device is to be designed and produced in a way that ensures that any risks associated with the use of the device are acceptable risks when weighed against the intended benefit to the patient, and compatible with a high level of protection of health and safety.
Further, Essential Principle 2(2) requires, among other things, that in selecting appropriate solutions for the design and construction of a medical device so as to minimise any risks associated with the use of the device, the manufacturer must:
- identify hazards and associated risks associated both its intended purpose and foreseeable misuse of the device
- eliminate or reduce the identified risks as far as possible by adopting a policy of inherently safe design and construction
- ensure adequate protection measures are taken, including alarms if necessary, in relation to any risks that cannot be eliminated
- inform users of any residual risks that may arise due to any shortcomings of the protection measures adopted.
Essential Principle 12.1 (5)2 requires that manufacturers of programmed or programmable medical devices, or software that is a medical device, design, produce and maintain with regard to best practice in relation to software, security and engineering to provide cybersecurity of the device, including to:
- provide protection against unauthorised access, unauthorised influence or unauthorised manipulation
- minimise risks associated with known cybersecurity vulnerabilities
- facilitate the application of updates, patches, compensating controls and other improvements, including making available sufficient information for a user to make decision with respect to the safety of applying or not applying these disclose known vulnerabilities in the device or its components and associated mitigations.
Cyber security considerations that a manufacturer may need to address to comply with these Essential Principles will depend on the type of device, but may include:
- off-label use of devices by clinicians in certain situations
- malicious and unauthorised access to or modification of a device
- exploitation of known vulnerabilities in the device software or hardware
- unsupported user modification of devices to customise a device to perceived needs or preferences
- use of device in operating environments that are not or may not be secure.
Additional examples of cyber security considerations for manufacturers and sponsors as they relate to a number of the Essential Principles are highlighted in Table 1.
Where appropriate, these considerations require the manufacturer to act to reduce or manage associated risk and these actions should be documented in the manufacturer's quality management system and/or risk management system.
| Essential Principle | Cyber security considerations |
|---|---|
| 1. Use of medical devices not to compromise health and safety |
|
| 2. Design and construction of medical devices to conform to safety principles |
|
| 3. Medical devices to be suitable for intended purpose |
|
| 4. Long-term safety |
|
| 5. Medical devices not to be adversely affected by transport or storage |
|
| 6. Benefit of medical devices to outweigh any undesirable effects |
|
| 9. Construction and environmental properties |
|
| 10. Medical devices with a measuring function |
|
| 12. Medical devices connected to or equipped with an energy source |
|
| 13. Information to be provided with medical devices |
|
Relevant standards
The application of standards is one way to demonstrate that medical devices are compliant with the Essential Principles, although their use is not mandated by the TGA.
Medical devices that have cyber security risk/s are highly variable in their components and operate in a variety of environments, resulting in many relevant standards.
The matrix below (Table 2) presents a summary of standards recognised as being suitable to meet regulatory requirements for cyber security of medical devices, alongside the relevant Essential Principle that may be demonstrated.
Alongside relevant standards, other risk management strategies can be adopted if they are generally acknowledged state of the art.
As technology evolves and new standards and guidelines are developed, manufacturers and sponsors will need to be aware of the changing state of the art relevant to their devices.
Manufacturers and sponsors are encouraged to review international guidance and publications concerning medical device cyber security, and review established and emerging practices from the broader cyber security sector, many of which have been applied in complex industry environments where risk reduction is a primary focus.
| Standard* | Scope | EP1 | EP2 | EP3 | EP4 | EP5 | EP6 | EP9 | EP10 | EP12 | EP13 |
|---|---|---|---|---|---|---|---|---|---|---|---|
ISO 14971 Medical devices—Application of risk management to medical devices | A process for a manufacturer to identify the hazards associated with medical devices, to estimate and evaluate the associated risks, to control these risks, and to monitor the effectiveness of the controls. | Yes | Yes | Yes | Yes | - | Yes | Yes | - | Yes | - |
ISO 13485 Medical device—Quality management systems—Requirements for regulatory purposes | Specifies requirements for QMS where an organisation needs to demonstrate its ability to provide medical devices and related services that consistently meet customer and applicable regulatory requirements. | Yes | Yes | Yes | Yes | Yes | - | - | Yes | - | - |
IEC 62304 Medical device software—Software life cycle processes | Defines the life cycle requirements for medical device software: the set of processes, activities, and tasks including development, maintenance, configuration management and problem resolution.
| - | Yes | - | Yes | Yes | Yes | Yes | - | Yes | Yes |
IEC 60601 (series) Medical electrical equipment—General requirements for basic safety and essential performance | Widely accepted benchmark for medical electrical equipment. The standards covers safety and performance for electrical medical equipment and helps to ensure that no single electrical, mechanical or functional failure shall pose an unacceptable risk to patients and operators. | - | Yes | - | - | Yes | - | Yes | Yes | Yes | - |
IEC 62366-1 Medical devices—Part 1: Application of usability engineering to medical devices | Specifies a process for a manufacturer to analyse, specify, develop and evaluate the usability of a medical device as it related to safety | Yes | Yes | Yes | Yes | - | - | Yes | - | Yes | Yes |
IEC TR 62366-2 Medical devices—Part 2: Guidance on the application of usability engineering to medical devices | Contains background information and provides guidance that address specific areas that experience suggests can be helpful for those implementing a usability engineering (human factors engineering) process | Yes | Yes | Yes | Yes | - | Yes | Yes | - | Yes | - |
UL 2900-1 Software Cybersecurity for Network-Connectable Products, Part 1: General Requirements | Applies to network-connectable products that shall be evaluated and tested for vulnerabilities, software weaknesses and malware: (i) developer risk management process requirements; (ii) methods to test vulnerabilities, software weaknesses and malware; and (iii) security risk control requirements. | Yes | Yes | Yes | Yes | - | - | Yes | - | Yes | - |
UL 2900-2-1 Software Cybersecurity for Network-Connectable Products, Part 2-1: Particular Requirements for Network Connectable Components of Healthcare and Wellness Systems | Particular Requirements for Network Connectable Components of Healthcare and Wellness Systems. It is a security evaluation standard that applies to medical devices, accessories to medical devices and medical device data systems. | Yes | Yes | Yes | Yes | - | - | Yes | - | Yes | - |
IEC 80001 (series) Application of risk management for IT-networks incorporating medical devices | 80001 series of standards define roles, responsibilities and activities for risk management of IT-networks incorporating medical devices. Focus is on safety, effectiveness, data security and system security. | Yes | Yes | Yes | - | - | - | Yes | - | - | Yes |
AAMI/UL 2800 Safety and security requirements of interoperable medical systems | Defines safety specifications that a medical devices interface should be labelled in order to operate in safe conditions. Focuses on risks associated with interoperability within the integrated clinical environment. | - | Yes | Yes | - | - | - | Yes | - | Yes | Yes |
AAMI TIR 57 Principles for medical device security—risk management | Methods to perform information security risk management for medical device within the context of ISO 14971. Incorporates the view of risk management from IEC 80001-1. | Yes | Yes | Yes | Yes | - | Yes | Yes | - | Yes | - |
IEC 80002(series) Medical device software | Provides guidance on the application of ISO 14971 to medical device software, methods for validation of software for medical devices including any software used in device design, testing, component acceptance, manufacturing, labelling, packaging, distribution and complaint handling or to automate any other aspect of a medical device quality system. | Yes | Yes | Yes | Yes | - | Yes | Yes | - | Yes | Yes |
ISO/IEC 15408 (series) Evaluation criteria for IT security | Common criteria. Establishes general concepts and principles of IT security evaluation, models for evaluation of security properties of IT products. | Yes | Yes | Yes | Yes | - | - | Yes | - | Yes | - |
IEC 82304-1 Health software—Part 1: general requirements for product safety | Covers entire lifecycle including design, development, validation, installation, maintenance, and disposal of health software products. Covers safety and security of health software products designed to operate on general computing platforms and intended to be placed on the market without dedicated hardware. | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
ISO/IEC 29147 Information technology — Security techniques — Vulnerability disclosure | Details the methods a vendor should use for the disclosure of potential vulnerabilities in products and online services. | Yes | - | - | Yes | - | - | Yes | - | Yes | Yes |
ISO/IEC 30111 Information technology—security techniques—vulnerability handling process | Explains how to process and resolve potential vulnerability information in a product or online service. | Yes | Yes | Yes | Yes | Yes | Yes | Yes | - | Yes | Yes |
ISO 27799 Health informatics—Information security management in health using ISO/IEC 27002 | Explains organisational information security standards and information security management practices including the selection, implementation and management of controls taking into consideration the organisation's information security risk environment(s). | - | - | - | Yes | Yes | - | Yes | - | - | Yes |
ISO 14708-1 Implants for surgery -- Active implantable medical devices -- Part 1: General requirements for safety, marking and for information to be provided by the manufacturer | Specified the general requirements for active implantable medical devices and safety requirements including those for electrical, mechanical, thermal, and biocompatibility hazards. The standard is also applicable to some non-implantable parts and accessories | Yes | Yes | Yes | - | - | - | Yes | - | Yes | Yes |
IEC 61010-2-101 Safety requirements for electrical equipment for measurement, control, and laboratory use—Part 2-101: Particular requirements for in vitro diagnostic (IVD) medical equipment | Applies to equipment intended for in vitro diagnostic (IVD) medical purposes, including self-test IVD medical purposes. | Yes | Yes | - | - | - | - | Yes | Yes | Yes | - |
*Use the current version of each standard as appropriate.
Cyber security key terms
Vulnerabilities
Vulnerabilities are weaknesses in computer software code, hardware designs, information systems, security procedures, internal controls, or human behaviour that could be exploited by a threat.
Vulnerabilities are typically made known to the public once a verified patch exists; this can be via active vulnerability monitoring (cyber security risk monitoring) or by notification to the manufacturer/sponsor by a third-party.
When a vulnerability is identified a manufacturer must assess the risk posed to the safe use of the medical device and decide if Corrective and Preventative Action (CAPA) is required based on the level of risk.
Even if the risk is assessed to be acceptable without implementing specific mitigations or patches due to no known active exploitation, a low likelihood of exploitation, or negligible potential risk of harm to patients, this should still be documented as part of continuous risk management.
Essential Principle 2 requires that manufacturers eliminate or reduce risk as far as possible and inform users of the residual risk that arises from any shortcoming of the protection measures adopted.
Many vulnerabilities remain intentionally undisclosed and may be leveraged by adversaries in a ‘zero day’ attack. This is an attack that exploits a vulnerability that the vendor or development may be unaware of.
Exploits
An exploit is a piece of code, software or tools that takes advantage of (one or more) vulnerabilities in the software or hardware to gain access to a network or system.
Numerous exploits are publicly accessible and are packaged as executables or source code. These exploits may also be packaged into toolsets for improved usability.
Threats
Threats can emerge with the existence of vulnerabilities and adversarial motives to exploit these vulnerabilities—a situation that has the potential to cause harm.
For example, the threat on patient privacy, such that data may be exposed to unauthorised individuals; or the threat on patient safety, such that a compromised device may no longer complete its intended task.
Black hat adversaries may instigate an attack by strategically using several exploits to realise threats and achieve their objective.
Figure 1. Vulnerabilities, exploits, threats, risks and adversaries
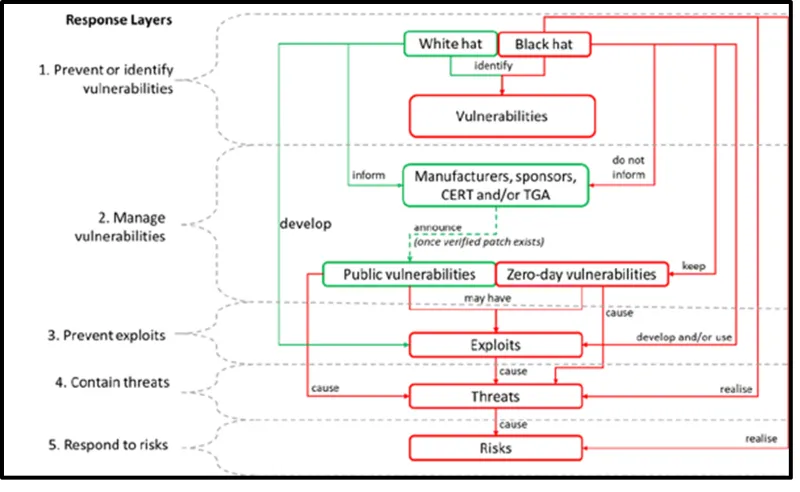
The image shows a flowchart titled "Response Layers" illustrating the process of identifying and managing cybersecurity threats. It's divided into five main layers:
- Prevent or identify vulnerabilities
- Manage vulnerabilities
- Prevent exploits
- Contain threats
- Respond to risks.
The chart uses green and red boxes to differentiate between "White hat" and "Black hat" activities:
White hat activities:
- Identify vulnerabilities
- Inform manufacturers, sponsors, CERT and/or TGA
- Develop public vulnerabilities.
Black hat activities:
- Identify vulnerabilities
- Develop and/or use zero-day vulnerabilities
- Cause exploits
- Cause threats
- Cause risks.
Key relationships shown:
- Both white and black hats identify vulnerabilities
- White hats inform relevant parties, while black hats do not
- Public vulnerabilities may lead to exploits
- Zero-day vulnerabilities are kept secret and lead to exploits
- Exploits cause threats, which cause risks.
Arrows connect these elements, showing the flow from vulnerabilities to exploits, threats, and ultimately risks.
The chart emphasises the contrast between ethical (white hat) and malicious (black hat) approaches to cybersecurity.
Cyber security risk monitoring
To ensure that a medical device included in the ARTG continues to meet the requirements of the Essential Principles, a manufacturer or sponsor must demonstrate how they will gather information regarding emerging risks, including cyber security vulnerabilities that may impact the safe operation of their medical device and how these will be addressed.
In order to monitor for vulnerabilities that will affect a given device, the manufacturer should maintain a Software Bill of Materials (SBOM) to better assess risk should a vulnerability be discovered.
Manufacturers should share information with the TGA, (see Post-market guidance), and the wider industry regarding cyber security vulnerabilities that are discovered and threats that emerge.
In a case where cyber security vulnerabilities, threats and risks pose an immediate and significant threat to the health and safety of users or will result in deficiencies or potential deficiencies to the safety, quality, performance or presentation of the device, this information must be shared with the TGA and a corrective and preventative action taken.
Pre-market guidance
Pre-market regulatory requirements
Sponsors intending to include a medical device in the ARTG for supply in Australia need to meet their legal obligations under the Act and MD Regulations. In demonstrating compliance with the Essential Principles, the Sponsor needs to demonstrate that cyber security risks have been addressed.
We have a risk-based approach to the regulation of medical devices.
The level of scrutiny by the TGA of a device before it is placed in the ARTG and supplied in Australia depends on the risk posed by the device.
The lowest risk medical devices, Class 1 devices, are not assessed by the TGA before inclusion in the ARTG.
For all classes of medical devices, evidence is required to be made available when requested by the TGA to demonstrate that medical device risk, including cyber security risk is being managed by appropriate quality management systems and risk management frameworks.
The regulations specify that some applications are subject to mandatory application audits, with other types of applications subject to non-mandatory application audits.
All medical devices that include software are susceptible to cyber security risks.
Manufacturers of medical devices must demonstrate how cyber security risk has been minimised during the design, development, manufacturing, and supply of a medical device, and how post-market requirements will be satisfied.
These activities are critical to reduce the likelihood of cyber-security vulnerability being exploited leading to unacceptable risk to a patient, and for the management of emerging and ongoing cyber security risk and they should be documented in a manufacturer's quality management system.
Alongside the TGA's regulatory requirements for device safety, performance and quality, manufacturers are reminded that some devices may also have other regulatory requirements that need to be met, for example, the Office of the Australian Information Commissioner's Notifiable Data Breach Scheme under the Privacy Act 1988.
Development approach
To meet the requirements of the relevant Essential Principles, a manufacturer is required to eliminate identified cyber security risk or reduce the risk to an acceptable level.
The potential for new cyber security risks that will emerge over the usable life of the device must also be considered and planned for, with upgrade pathways proactively developed where appropriate to address these issues once the device is on the market.
Manufacturers should also proactively consider how to reduce risks associated with device obsolescence.
To reduce cyber security risk throughout the design and development phases, there are two approaches that assist in understanding cyber security risk as early as possible.
Consideration of these approaches also assists with compliance with the Essential Principles.
They include:
- Secure by design: developing an understanding of cyber security vulnerabilities associated with the medical device and the potential risk during the initial design and development phase. Early assessment allows adaptable cyber security measures to be incorporated in the device design, such as minimisation of the potential attack surface, secure code, etc. The Software Assurance Forum for Excellence in Code (SAFECode) publishes information concerning secure software development.4
- Quality by design: building on the secure by design approach, quality by design involves understanding and mitigating the potential risks introduced with each function of the medical device, its manufacturing process and the environment in which the device is used. These risks may include cyber security, privacy, usability, safety and other associated risks. While an increase in functions (e.g. Bluetooth connectivity) may lead to improved usability, the way the function is designed, manufactured or used may also increase the device's exposure to cyber security vulnerabilities. More exposure increases the likelihood of a cyber security vulnerability being exploited, leading to potentially unacceptable risks. Early assessment allows for a stronger balance between functionality and cyber security.
Application of standards
The Essential Principles require that design solutions adopted by medical device manufacturers will have 'regard to the generally acknowledged state of the art'5
In many instances, this expectation is achieved by the application of standards, some of which are outlined in Relevant standards.
The standards outlined in Table 3 are generally expected as a baseline during the design and development of a medical device; however, depending on the device, compliance with the Essential Principles may necessitate implementation of additional standards (information in Relevant standards).
Manufacturers should be mindful that application of standards alone does not guarantee compliance to the Essential Principles.
Additionally, application of standards does not guarantee adequate cyber security given the rapidly changing pace of cyber-attacks against the typical timeframes for standards development and implementation.
| Standard* | Scope |
|---|---|
| ISO 14971 | Medical devices - Application of risk management to medical devices |
| ISO 13485 | Medical devices - Quality management systems—Requirements for regulatory purposes |
| IEC 62304 | Medical device software - Software life cycle processes |
| IEC 60601 (series) | Medical electrical equipment - General requirements for basic safety and essential performance |
* Use the current version of each standard as appropriate.
Risk management strategies
Risks that must be managed are detailed in the Essential Principles.
Broadly, these include risks associated with the intended use of the device, long term safety, transport and storage, reasonably foreseeable environmental conditions, and unavailability of maintenance and calibration.
The development of risk management strategies - the continuous approach to identifying, estimating and reducing risk - is required in order for a medical device to comply with the Essential Principles; cyber security risk management can be readily included in these strategies.
A separate cyber security risk assessment in addition to the product risk assessment is an acceptable approach.
Two potential strategies to manage risk are detailed below, including the process outlined in ISO 14971 and the USA's National Institute of Standards and Technology's (NIST) cyber security framework.
While ISO 14971 is the most commonly applied risk management strategy, others can be used as long as they ensure a manufacturer is adequately assessing, controlling and monitoring risks.
ISO 14971 standard
The ISO 14971 standard specifies a process through which the manufacturer of a medical device can identify hazards associated with a medical device, estimate and evaluate the risks associated with these hazards, control these risks, and monitor the effectiveness of that control.
The following qualitative levels of severity of patient harm, based on descriptions in ISO 14971, could be used in a cyber security risk assessment:
- negligible: Inconvenience or temporary discomfort
- minor: Results in temporary injury or impairment not requiring professional medical intervention
- serious: Results in injury or impairment requiring professional medical intervention
- critical: Results in permanent impairment or life-threatening injury
- catastrophic: Results in patient death.
The quantity of patients affected by the risk may warrant an increase in the severity of harm, for example it may be more appropriate to describe a critical level of harm to many patients as catastrophic.
The following summary is provided as an example of a risk management process under ISO 149716:
- Implement a risk management framework
- Establish the risk management process
- Establish relevant roles and responsibilities
- Establish appropriate documentation
- Create a version controlled risk management file
- Define the intended use of the medical device
- Identify hazards
- What are the known cyber security vulnerabilities?
- Define hazardous situations and foreseeable use
- Develop cyber security scenarios that are likely in the foreseeable use
- Estimate the level of risk
- How likely is it that cyber security vulnerabilities will be exploited to create unacceptable levels of risk?
- Evaluate the identified risk
- Is the risk acceptable?
- If not acceptable, it will need to be reduced to an acceptable level
- Risk control
- Has the cyber security risk been reduced as far as possible or to a level that is outweighed by the benefits of the component/function that introduced the risk?
- Evaluate entire product risk acceptability
- Is the risk acceptable?
- Do the benefits of the medical device outweigh the risks?
- Risk management reporting
- Complete a review and prepare appropriate documentation and reports prior to seeking regulatory approval.
- Post-market risk management
- Complete activities for risk minimisation from a total product life cycle perspective; internal risk management audits, corrective and preventative action (CAPAs), etc.
National Institute of Standards and Technology
Development of a risk management strategy in line with the USA's National Institute of Standards and Technology's (NIST) cyber security framework is an approach used as a way to address cyber security risks. Originally developed for critical infrastructure, the framework is also beneficial for manufacturers of medical devices and the broader healthcare ecosystem.
The framework describes a series of concurrent and continuous cyber security functions that underpin a cyber security risk management strategy for both pre- and post-market phases7:
- Identify: Develop an organisational understanding of cyber security to effectively manage cyber security risk associated with medical devices
- Protect: Develop and implement appropriate actions to ensure that a medical device can safely deliver its intended function, balancing security and usability
- Detect: Develop and implement appropriate activities to identify the occurrence of a cyber security event that changes the risk profile of a medical device
- Respond: Take appropriate action to ensure that cyber security risk is minimised for a medical device with a new risk profile
- Recover: Implement activities to increase medical device cyber resilience and to restore any capabilities or services that were impaired due to a cyber security incident.
Implementing a cyber security risk management strategy that is based on this framework may assist in meeting the requirement for a medical device to obtain and maintain regulatory compliance in Australia.
Management of manufacturing and supply chain
Medical device manufacturers need to consider the cyber security practices of their manufacturing and supply chain, ensuring that relevant components used within or for the construction of the device are appropriately cyber secure, and will meet the requirements of the Essential Principles, in particular:
- Essential Principle 2: Design and construction of medical devices to conform with safety principles
- Essential Principle 4: Long-term safety
- Essential Principle 5: Medical devices not to be adversely affected by transport or storage
- Essential Principle 9: Construction and environmental properties.
Contractual negotiations and agreements should clearly outline cyber security expectations from the medical device manufacturer or sponsor responsible for the device once it is supplied in Australia.
Manufacturers should investigate and ask questions to understand the cyber security practices and response plans of their suppliers and any platforms that their products will operate on or be distributed through (this includes mobile devices, web services and cloud services).
On-going monitoring of practices should also be implemented, and manufacturers should act in a timely manner should they discover a cyber security (or other) issue from a component within their supply chain.
Agreements should include expectations about cyber security practices of third parties to ensure the confidentiality, integrity and availability of applicable systems.
Where appropriate, thresholds and timelines for supply chain reporting of cyber security incidents should be agreed
Provision of information for users
Essential Principle 9 requires, among other things, that a medical device manufacturer must ensure that a medical device is designed and produced in a way that ensures that, as far as practicable, the risks associated with reasonably foreseeable environmental conditions are removed or minimised8.
To meet this requirement and those of Essential Principle 13 (Information to be provided with medical device), appropriate information on cyber security must be provided to users of medical devices.
This should include plain-language information for users with little or no cyber education, and technical language information for those with more advanced understanding.
Considerations for cyber security specific information that may need to be provided in line with Essential Principle 13 can be found in Table 1.
Effective communication is required for consumers to understand risk and give informed consent to treatment.
This can be a challenge when both the clinician and the consumer may lack specific expertise on medical device cyber security, compounded by the rapidly changing pace of cyber security.
Because of this potential mutual lack of cyber expertise, the requirements for manufacturers to provide clear, high quality and usable information to clinicians and consumers about cyber security risks and how to mitigate them are vitally important.
Clinicians need to be armed with the information to have a meaningful discussion with the patient about the risks and benefits of a particular device they are prescribing, including cyber security risk.
This information needs to be in a language that is relevant to them, and their patients.
In the case of high-risk devices, clinicians must also have access to information to understand how and when to apply an update to a device.
Provision of information is also important for consumer focused medical devices, where the device may be used in a home environment (with limited cyber security protection) or a public environment which by nature is highly accessible.
As healthcare service providers increasingly strive to create a cyber secure environment, medical device manufacturers and sponsors supplying to these service providers will be asked for more specific information on cyber security risk mitigation measures during procurement activities.
Collaboration between these organisations is essential to creating a more cyber secure healthcare environment.
The USA's National Electrical Manufacturers Association (NEMA) provides an example form that manufacturers might consider when providing information to healthcare services providers (see Manufacturer Disclosure Statement for Medical Device Security).
Further, a list of potential questions suggested for these procurement teams are listed in our medical device cyber security guidance for users of medical devices.
These include:
- What security measures have been built into the device?
- What measures are in place to protect patient safety?
- What measures are in place to protect the confidentiality, availability and integrity of patient data?
- How has security been addressed at the user interface level?
- What security protocols and frameworks have been used?
- What are the known cyber security vulnerabilities for the device?
- Has the manufacturer assessed the cyber security of key components within the device (i.e., development environment, build tools, and the supply chain)?
- Does the manufacturer/sponsor provide an ongoing service to manage the security of the medical device(s), and how will they respond to future cyber security incidents?
- A medical device often has a long lifecycle—does the manufacturer/sponsor have enough resources to support the security requirements throughout the lifecycle?
- How is data from the device logged and stored? Are third-party cloud services used and if so, what are their privacy and security policies? Is the data stored onshore?
- How will the manufacturer respond in the future if a medical device cyber security incident occurs?
- Has the company experienced any cyber security issues over the past 12 months and how were these managed?
Technical cyber security considerations
There are a number of technical cyber security considerations that a manufacturer should address during the pre-market development of a medical device to help ensure that cyber security risks to patient safety are designed out, removed, eliminated, reduced or otherwise managed.
A number of these considerations are detailed here; however, manufacturers should be aware that technical considerations will vary depending on the device in question, the intended use, and the environment of use.
Refer to ACSC (Australian Cyber Security Centre), and in particular, the Essential Eight baseline mitigation strategies to protect against cyber threats.
Modularised design architecture
- It is best practice to modularise or partition aspects of the design architecture to enable independent function of modules for cyber security.
- A modularised approach promotes medical devices that can be updated and adapted to changes in the cyber security risk profile over the total life cycle of the product.
- A secure operating platform, such as a security-verified microkernel, verifies the design architecture and enforces component separation in the designed partitions in order to prevent a critical software component from being negatively affected by other software components and cyber security attacks targeting them.
- Smaller components are easier to assess for cyber resilience, by application of methods including formal mathematical proofs. Reuse of validated or verified trustworthy modules in different devices will improve overall cyber security, with reduced effort.
Cyber security assessment and penetration testing
- Consider implementing penetration testing initiatives (commensurate with risk level) to validate the effectiveness of medical device cyber security measures and internal risk management practices, and identify unknown vulnerabilities:
- Invasive tests involving simulated malicious attacks to evaluate the effectiveness of managing possible and probable attacks, e.g. malicious input, authentication bypass, and illicit operation.
- Cyber security performance testing should be performed by a qualified party independent of the development team. Collaboration or partnership with 'white-hat' hackers, biomedical engineering teams and cyber security professionals is recommended.
- Utilise information from recognised organisations and industry groups regarding application security risks. One example of an accessible source is the Open Web Application Security Project which describes a Top 10 most serious web application security risks on a yearly basis.
- It is recognised that some critical systems may not be removed from production for testing, and if feasible, a twin system for testing is recommended to overcome this. Network threat modelling using approaches such as the MITRE ATT&CK framework are also recommended to improve the cyber resilience of devices.9
- Regular code review and penetration testing should cover assessment of common cyber security vulnerabilities (like the examples in Appendix 1: Known vulnerabilities) through database checks, use of known exploits and tools like vulnerability scanners, or software behaviour analysis using specific scenarios. Cyber security risks that should be assessed include:
- Insufficient use of appropriate encryption and authentication protocols
- Use of insecure function calls, e.g. causing overflow type of vulnerabilities
- Insufficient protection for security credentials, e.g. hard-coded passwords
- Insufficient information security capabilities, e.g. missing or improper use of confidentiality, integrity and availability measures
- (Un)intentionally left debugging features and comments, e.g. debugging hooks, open JTAG ports
- Improper use of control statements, e.g. improper checks for unusual or exceptional conditions
- Wrong implementation of algorithms and protocols, e.g. OpenSSL Heartbleed
- Flaws in algorithm and protocol designs, e.g. Compression Ratio Info-leak Made Easy (CRIME) vulnerability of TLS Compression
- Malicious codes and code segments, e.g. malwares such as virus and worms
- Software components development through an unknown or incompetent development process, i.e. software of unknown provenance (SOUP)
- Listed (e.g. NVD, CERT, ACSC) vulnerabilities for off-the-shelf components (kernel, driver, firmware, application), libraries and API
- Lack of input sanitation and data validation, e.g. allowing potential injection attacks
- Checking potential vulnerabilities through control flow analysis.
- Take action on outcomes of penetration testing by assessing the risk(s) of the affected functions and consider solutions that address the risk(s) according to Essential Principle 2.
- Continual assessment of the threat landscape and up to date intelligence on new and emerging vulnerabilities is vital to cyber security assessment.
Operating platform security
- Assessment of the cyber security (under the development approach) of third-party operating systems and hardware platforms needs to be completed in order to meet the Essential Principles (EPs), in particular EP 2 (Design and construction of medical devices to confirm with safety principles), EP 3 (Medical devices to be suitable for intended purpose) and EP 9 (Construction and environmental properties).
- This is particularly critical for software development where the product is intended to operate on a consumer mobile device or utilise a web or cloud service. It is required that the manufacturer or sponsor will have assessed the cyber security risks introduced by the third-party platform and inform the user where there is residual risk, in order to meet the requirements of the Essential Principles.
- High-level considerations include the cyber security protections and support that a third-party provides for its platform (covering differential responsibilities, processes and risks specific to the medical device domain), the ability to remove or disable unused functions, its default network security, and its accessibility if the user is expected to complete patching and performance updates.
- When possible, reduce the number and complexity of operating system components to reduce the attack surface, e.g. by using a simplified kernel design, or a stripped down operating system.
- When possible, implement code signing for firmware updates. These signatures include a signed hash of the firmware code which can be checked by the device before installing. An incorrect signature may indicate that the firmware is from an unauthorised (potentially malicious) source or that the firmware code has been tampered with.
Update pathways
- Manufacturers must consider the risks associated with available update methods and pathways, whether manual, remote access, continual updating using cloud/virtual systems, or another approach. Additionally, manufacturers must consider the ability for secure updating of a medical device during its lifecycle to account for emerging cyber risks, and demonstrate that the approach is in alignment with current state of the art practice.
Trusted access and content provision
- Manufacturers and sponsors are encouraged to implement trusted access measures for network connected devices to prevent unauthorised access and to reduce cyber security risk. This should focus on securing activities that will be undertaken by the medical device user and ensuring the device can only access networks that are absolutely necessary. Measures that manufacturers should consider include:
- Consider both physical and network access requirements—this might include removal of internet accessibility and direct network connectivity where appropriate and physically locking a device
- Incorporate multi-factor authentication, build in state-of-the-art access requirements (e.g. password, biometric, smartcard), account lockout protocols, and automatic timed methods to terminate sessions where appropriate
- Establish logs to ensure traceable access to the device and audit logs to ensure trusted and credentialed access
- Utilise user profiles that limit device access and privileges, balancing access and security (role-based access).
- Encryption of medical device data is recommended, both at rest and in transit, where appropriate.
- Manufacturers need to ensure that, as far as practicable, risks associated with the foreseeable environmental conditions are minimised which includes security risks of the networks on which a medical device is intended to operate on (Essential Principle 9 Construction and environmental properties - see Table 1).
Refer to the ACSC (Australian Cyber Security Centre) website for more details.
Post-market guidance
Regulatory requirements
We will always assess compliance with the Essential Principles against the current risk environment, regardless of which risks existed when the device was included in the ARTG.
This means that risks identified on cyber.gov.au will also be considered as representative of the current risk environment.Evidence of compliance with the Essential Principles, and other legislation, must be supplied to us if requested.
The inclusion of a medical device in the ARTG is subject to certain statutory conditions which include, for example, an obligation to maintain sufficient information to substantiate compliance with the Essential Principles or have procedures in place with the manufacturer to ensure such information can be obtained10.
Breaching the conditions of the inclusion of a medical device may lead to suspension or cancellation of the entry for that device from the ARTG11, may be an offence12, and may contravene a civil penalty provision13.
Consistent with these legislative requirements and in line with a total product life cycle (TPLC) strategy, once a medical device has been included in the ARTG, it must continue to meet the requirements of the Essential Principles to remain in the ARTG.
Risk management and quality management systems must be updated appropriately over the life cycle of a device to maintain inclusion in the ARTG. It is critical that the change management process, e.g. as outlined in IEC 62304 standard, is documented to clearly outline how risk and quality management systems have been modified as the risk profile of the medical device evolves.
Therapeutic Goods Act 1989 - Chapter 4, Part 4-5, Division 2, section 41FN(3)
41FN Conditions applying automatically
(3) The inclusion of a kind of medical device in the Register is subject to conditions that:
- at all times while the inclusion in the Register has effect, the person in relation to whom the kind of device is included in the Register:
- has available sufficient information to substantiate compliance with the Essential Principles; or
- has procedures in place, including a written agreement with the manufacturer of the kind of devices setting out the matters required by the regulations, to ensure that such information can be obtained from the manufacturer within the period specified in the regulations; and
- at all times while the inclusion in the Register has effect, the person in relation to whom the kind of device is included in the Register:
- has available sufficient information to substantiate that the conformity assessment procedures have been applied to the kind of medical device or that requirements, comparable to those procedures, have been applied to the kind of medical device to the satisfaction of an overseas regulator; or
- has available information relating to changes to the kind of medical device, the product range, and quality management system, of the manufacturer of the device; or
- has procedures in place, including a written agreement with the manufacturer of the kind of devices setting out the matters required by the regulations, to ensure that such information can be obtained from the manufacturer within the period specified in the regulations; and
- at any time while the inclusion in the Register has effect, the person in relation to whom the kind of device is included in the Register will, if asked to do so by the Secretary, give the information to the Secretary; and
- the person in relation to whom the kind of device is included in the Register will give information of a kind mentioned in subsection 41MP(2) or 41MPA(2) to the Secretary within the period specified in the regulations; and
- the person in relation to whom the kind of device is included in the Register will give the manufacturer of the kind of medical device information relevant to:
- the manufacturer's obligations under the conformity assessment procedures or requirements comparable to those procedures; and
- whether medical devices of that kind comply with the Essential Principles.
Cyber security risk
Cyber security risk must be considered as part of the post-market risk management process (e.g. ISO 14971, NIST cyber security framework) and is an ongoing activity.
As with other risks, the changing nature of cyber security risks means that it cannot be mitigated through pre-market controls alone and requires continued management.
Cyber security risk monitoring and management must be an integral aspect of the post-market monitoring activities conducted by manufacturers and sponsors.
Cyber security is an ongoing activity.
As with other risks, it is important for medical device manufacturers and sponsors to develop an understanding of how to assess cyber security risk.
To do this effectively it is important to build a robust understanding of the relationship between cyber security vulnerabilities, exploits, and threats.
This will assist a manufacturer or sponsor in understanding which course of action is required in response to the changed medical device cyber security risk profile including:
- device recalls
- product alert or corrections
- routine updates
- adverse event reports to the TGA.
Figure 1 details the high-level relationship between vulnerabilities, exploits, threats and risk, and the people who have adversary capabilities, commonly known as white hat and black hat.
In addition, users of medical devices can unwittingly introduce cyber security risk by attempting to make unauthorised modifications to enhance the device for their perceived needs.
In some cases, these modifications may be unintentional.
Further, insider threats present a challenge to both manufacturers and users of medical devices.
Employees, contractors or partners wishing to cause harm represent a significant source of threat.
Having authorised access allows insiders to potentially compromise confidentiality, integrity or availability of medical devices and their networks and data.
Malicious or accidental insider access to a device or deletion, alteration, falsification, or unauthorised sharing of patient data is a real challenge that manufacturers need to be aware of, identify and address.
Cyber security threat and risk response
To remain compliant with the Essential Principles a manufacturer or sponsor must establish, document, and update quality management and risk management systems throughout the lifecycle of a medical device.
Documenting the effectiveness of any product correction or market action is required as part of this process.
This involves an ongoing process for identifying hazards associated with the safe use of the medical device, including cyber security vulnerabilities, threats, and estimating and evaluating the associated risks, controlling these risks, and taking corrective action where necessary.
Monitoring issues
As part of a total product lifecycle strategy and the sponsor's post-market obligations, ongoing monitoring and surveillance of safety and performance is required, including monitoring for cyber security issues.
This approach to monitoring cyber security intelligence and information should be clearly outlined during the development of the medical device.
Cyber security vulnerabilities, threats and risks may be identified by numerous different parties along the supply chain, including:
- the manufacturer (through an effective quality management system)
- the Australian sponsor(s) (through adverse event reports, complaints, and monitoring of Computer Emergency Response Team (CERT) alerts)
- TGA (through post-market monitoring and compliance activities)
- other regulators and government organisations such as the Australian Cyber Security Centre, who may notify the TGA
- a Cyber Security Operations Centre or Security Information and Event Management capability, either internal to the organisation or as a service provider
- white hat hackers and researchers, who may notify the TGA, sponsor or manufacturer
- users, including patients and consumers, health service providers, and administrators
- third-party audits (e.g. by clients), inspections by other regulators and other avenues
- media (traditional and social).
To effectively monitor for vulnerabilities that may affect a given device, the manufacturer should maintain a Software Bill of Materials (SBOM) to cross-reference for improved assessment of risk should a vulnerability be discovered.
If a cyber security vulnerability is identified through monitoring activities, the manufacturer should work with the source (where appropriate) to understand the issue and conduct a risk assessment.
The outcome of all cyber security monitoring must be documented as part of ongoing risk management, regardless of the level of risk that the activity identifies.
Cyber threat information sharing is an important component for a safe and secure digital ecosystem.
Information sharing enables parties along the supply chain, but especially the manufacturer and sponsor, to identify threats, assess associated risks, and share best practice approaches.
Information empowers organisations with knowledge to monitor threats and respond accordingly.
In Australia, the Australian Cyber Security Centre can facilitate general cyber security threat information sharing and monitoring.
International resources such as the NIST National Vulnerability Database are also useful sources of information.
We also encourages informal networks of manufacturers to share information on threats and recognises the value of information from international organisations (e.g. health focused Information Sharing and Analysis Organizations (ISAOs) in the USA).
Risk assessment
A manufacturer’s or sponsor's assessment of the risk of patient harm posed by a cyber security hazard that impacts the safety, quality, performance or presentation of a device should consider:
- The exploitability of the cyber security vulnerability or threat
- Estimating the likelihood of a cyber security exploit succeeding is difficult. Manufacturers or sponsors should consider using a cyber security vulnerability assessment tool or similar scoring system for rating vulnerabilities and determining the need for and urgency of the response. An example is the Common Vulnerability Scoring System (CVSS). Many factors are important to consider here, including ability to detect the vulnerability.
- The severity of patient harm if the vulnerability were to be exploited (Figure 2)14
- Manufacturers or sponsors should have a process for assessing the severity of patient harm should the cyber security vulnerability be exploited. For example, the qualitative severity levels of patient harm, as described in ISO 14971.
Manufacturers or sponsors can evaluate whether cyber security vulnerability creates potential risks associated with an adverse event, a medical device failure or a complaint, and understand if the risk of patient harm is:
- acceptable, with a low risk to the intended benefit or
- unacceptable, with a high risk to intended benefit.
Regardless of the outcome of the risk assessment, all risk assessment activities (including the cyber security monitoring activities) must be recorded, demonstrating application of the risk management strategy (e.g. application of ISO 14971) outlined as part of the pre-market activities.
This must include corrective and preventative action (CAPA) plans and incident response activities. Quality management systems should also be updated, if applicable.
Risk assessment should be a re-occurring activity with a frequency based on the level of risk and any new information that is uncovered.
Manufacturers must remediate cyber security vulnerabilities to reduce the risk of patient harm to an acceptable level.
- If the risk of patient harm is unacceptable, sponsors and manufacturers must take appropriate market action to remediate the cyber security vulnerability. This includes sharing relevant information with sponsors, regulators, customers and the wider user community, and implementing controls to adequately mitigate the risk. Reporting requirements must also be acted on.
- Where residual risk is acceptable, sponsors and manufacturers must proactively promote practices that continue to reduce cyber security risks. In circumstances where the medical device meets all relevant specifications and standards with no deficiencies in device safety, quality, performance or presentation, TGA notification may not be required. Instead, these risks should be disclosed directly with end users to support and promote best practice.
Updates and change control
Manufacturers must assess which course of action to take before making updates to medical devices (including to software).
Such a proposed change may require an associated market action, e.g. a recall, product alert, product correction, or quarantine.
Changes to software that do not have implications for safety, quality, performance or presentation generally do not require any form of market action.
However, the manufacturer should consider whether its certifying body should be notified of the change.
If sponsors or manufacturers are unclear as to whether a software update requires a type of market action, they should contact the Australian Recall Coordinator at recalls@health.gov.au for advice in the first instance.
Manufacturers and sponsors must update risk management systems following the rollout of updates to medical devices.
Procedure for recalls, product alerts and product corrections
For information relating to the procedure for recalls, product alerts and product corrections (PRAC) consult Recall coordinators for therapeutic goods and follow the steps as applicable.
Immediate action
Cyber security vulnerabilities, threats and risks may be discovered that pose an immediate and significant threat to the health and safety of users or public health.
Cyber security issues may also indicate that there has been actual or potential product tampering. In these cases, you may need to take immediate action before consulting the TGA.
If such a threat is found, sponsors must:
- consult available information relating to the Procedure for recalls, product alerts and product corrections (PRAC) and follow the steps to perform an immediate action
- contact us as soon as possible via:
| Phone |
|
Contact details for TGA, State and Territory Recall coordinators.
Market actions (other than immediate actions)
Market actions (other than immediate actions)
Cyber security vulnerabilities, threats and risks may be discovered that result in deficiencies or potential deficiencies to the safety, quality, performance, presentation or use of a medical device and require appropriate action to ensure the health and safety of users.
Sponsors should consider the appropriate Class, Type and Level of the market action in their notification to us.
Figure 2. Market action nomenclature
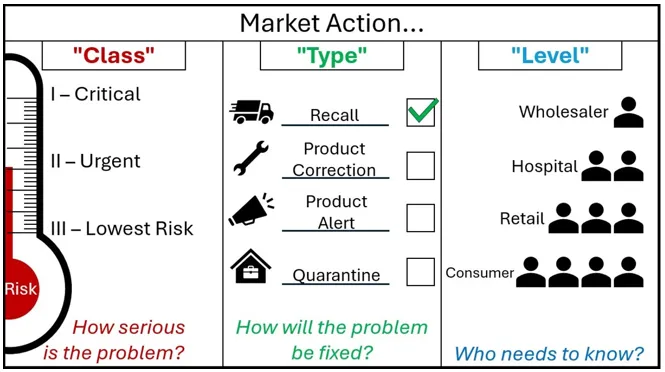
Other than immediate actions, do not contact your customers until after you receive our agreement to do so.
A graphic with the header 'Market Action'.
The graphic is split into 3 segments.
The first segment is marked 'Class - How serious is the Problem?'
It shows market action class as a thermometer marked 'Risk'. As the risk increases on the thermometer, the Class goes from Three - 'Lowest Risk', to Two 'Urgent', to One - 'Critical'.
The Second segment is marked 'Type - How will the problem be fixed?'.
It shows market action type as four options, each with an associated image. A speeding truck for the Recall action type, a spanner for the Product Correction Action type, a megaphone for the Product Alert Action type, and a locked box within a house for the Quarantine Action Type.
Next to each action are tickboxes, showing that these are choices that sponsors can select. For decoration purposes, the Recall Action type is ticked.
The third segment is marked 'Level - Who needs to know?'
It shows a small triangle of people, where each descending level involves more people who need to know about the action. The first level is Wholesaler, then Hospital, then Retail, and Consumer is the final layer at the bottom containing the most people who need to know. The type of market action for cyber security risks depends on the risk of patient harm and the nature of the deficiency. These need to be assessed on a case-by-case basis and are subject to change during our review of your draft action.
Examples of types of cyber security market actions
The PRAC defines four types of market actions:
- Recall: action to permanently remove products from the market. Customers may need to return the product to you, or dispose of the product on site.
- This action may be appropriate for high risk vulnerabilities to medical devices that are not able to be fixed in the field, or for those where a solution is not expected to be available within a suitable timeframe (to be determined in consultation with the TGA).
- Product correction: action undertaken to correct a specific or potential deficiency, including repair, modification, adjustment or re-labelling. A product correction may also include updates or changes to any accessories, operating instructions or software.
- This action may be appropriate for vulnerabilities to medical devices that are able to be corrected in the field and within a suitable timeframe.
- Product alert: issued to raise awareness about deficiencies, potential deficiencies or other concerns with the use of a product. Alerts are appropriate when stopping treatment could pose a greater risk than continued use of the affected product, the affected product cannot be recalled (i.e. implanted goods), or there are concerns that users are not following the precautions or existing instructions.
- This action may be suitable for vulnerabilities that cannot yet be fixed but where the risk of allowing the defective product to remain in use is deemed acceptable if managed appropriately.
- Quarantine: an action to suspend use of a product, pending further advice. Quarantines stop the use or distribution of a product while an ongoing investigation determines whether there are significant defects in safety, quality, efficacy or performance of a product.
- This action may be suitable if there are significant concerns that a vulnerability may exist, however it has not yet been substantiated. Use of the device may be suspended until the investigation is complete, at which point the action may escalate to a recall or correction, or the quarantine can be lifted and allow for continued use.
Examples of class of cyber security market action
Market actions related to cyber security could be class I, II or III.
- Class I – Critical safety-related: The problem presents a reasonable possibility of serious injury or death. For example:
- Software defects resulting in linear accelerators delivering the wrong radiation dose or delivering doses to the wrong location.
- Hardware or software failures in ventilators resulting in shut down during use.
- Class II – Urgent safety-related: The problem presents a reasonable possibility of temporary or minor injury, and/or the likelihood of serious injury or death is remote. For example:
- Infusion pumps giving visual or audible alarms due to software or hardware issues resulting in delay in infusion.
- Class III – Lowest risk: The problem is not likely to lead to injury, and/or the chance of a temporary or minor injury is remote. Class III actions usually address non-safety related problems.
Examples of notifications related to cyber security which do not need to be reported as a market action
Not all issues require a market action. You can notify your customers without alerting the TGA if:
- the medical device meets all specifications and standards, and
- There are no deficiencies in safety, quality, performance, presentation, or safety concerns due to customer misuse.
If you are unsure whether your proposed notification to end users requires reporting to the TGA, contact us for advice.
Other regulatory action
Alongside the market actions described above, the TGA has a range of other compliance tools it can use if risks identified in relation to a medical device are not managed appropriately. These include:
- Warnings and conditions: the TGA may need to engage with manufacturers/sponsors and make them aware of its concerns about any non-compliance with regulatory obligations. We may also take other action that affects the Sponsor, including imposing conditions on the inclusion of the kind of device in the ARTG.
- Suspensions and other enforcement action: the identification of contraventions of the Therapeutic Goods Act and/or the MD Regulations may result in the TGA suspending the kind of medical device from the ARTG, or taking other regulatory action, such as accepting an enforceable undertaking or issuing an infringement notice to the Sponsor.
- Cancellations and prosecution: the entry of a kind of medical device may be cancelled from the ARTG in certain circumstances specified in the Act. Breaches of the Act or MD Regulations may also result in the TGA initiating civil or criminal proceedings. For example, civil penalties and also criminal offences apply under the Act for importing, supplying or exporting a medical device that does not comply with the Essential Principles.
Appendix 1: Known vulnerabilities
The following list, which is not exhaustive, contains examples of known cyber security vulnerabilities for medical devices.
- Authentication bypass
- Buffer overflow
- Code injection
- Communication protocol vulnerability
- Credentials insufficiently protected
- Cross-site scripting
- Cryptographic issues
- Data authenticity insufficiently verified
- Debug service enabled by default
- Default password
- Exposed dangerous method or function
- Flash memory content insufficiently protected
- Hard-coded credentials
- Improper access control
- Improper authentication
- Improper authorisation
- Improper certificate validation
- Improper control of generation code
- Improper exception handling
- Improper input validation
- Improper restriction of communication channel to intended endpoints
- Improper restriction of operations within the bounds of a memory buffer
- Power consumption: improper restriction
- Reference information exposure
- Leftover debug code
- Man-in-the-middle
- Meltdown, Spectre and Spoiler
- Missing confidentiality
- Numeric errors
- Out-of-bounds read
- Path traversal
- PC operating system vulnerabilities
- Protection mechanism failure
- Relative path traversal
- Resource consumption uncontrolled
- Resource management errors
- Search path element uncontrolled
- Session expiration insufficient
- Unquoted search path or element
- Untrusted input accepted
- Vulnerable third-party software
- Weak password hashing algorithm
- XML external entity: improper restriction.
Appendix 2: The evolving cyber security landscape
We are responsible for the continued safety, quality and performance of medical devices affected by cyber-related issues.
Cyber security in Australia
The Australian Government released Australia's Cyber Security Strategy in 2016.
This strategy recognises that improving cyber security is a whole-of-economy challenge, and details priority actions to improve Australia's general cyber security posture, alongside supporting the growth of the local cyber security industry.
Putting the cyber security strategy into operation and providing a cyber secure environment that ensures stability for businesses and individuals to operate in is the responsibility of the Australian Government, specifically the Department of Defence and relevant agencies, including the Australian Signals Directorate (ASD) via the Australian Cyber Security Centre (ACSC).
Health technology and cyber security
The digitalisation of consumer and professional health technology is rapidly gathering traction, with increased application of wireless communication, cloud services, artificial intelligence (AI) and other technologies.
Some of this technology meets the definition of a medical device, while some does not.
Medical devices will increasingly be used in a wider variety of professional, personal and public environments, leading to new cyber security implications from an evolving cyber threat landscape.
Increased connectivity and digitisation of health technologies drives a changing cyber landscape, creating new vulnerabilities for medical devices.
Likewise, vulnerabilities from across the broader IT ecosystem can affect digital health technologies.
Figure 2. The evolving digital health and cyber landscapes
Diagram depicts a number of overlapping ovals showing that Digital Health/the Internet of Medical Things is a subset of the broader Internet of Things which cuts across all industries including healthcare, transport, manufacturing, energy, mining, industrial operations, etc.
Within the Digital Health/Internet of Medical Things domain, which includes consumer wearables, fitness trackers, apps, etc., sits the overlapping domains of healthcare information technology and regulated medical devices.
Healthcare information technology includes:
- electronic patient health records
- clinical information systems
- practice and enterprise management software, etc.
Regulated medical devices includes:
- medical imaging,
- surgical robots,
- in vitro diagnostic devices,
- communicative implants,
- software as a medical device, etc.
The diagram also depicts that there is an evolving cyber threat landscape that encapsulates the Internet of Things.
Driving this evolving cyber threat landscape is the digitisation of medical devices; further, vulnerabilities from the broader ecosystem can affect digital health technologies. The diagram depicts that vulnerabilities within the cyber threat landscape can cascade into exploits, threats and risks. Cyber security can help prevent vulnerabilities from being exploited.
Our role
As technology progresses, the capabilities and functionality of medical devices are becoming more digitised and interconnected.
Software in particular is becoming increasingly important and pervasive in healthcare.
As the digital complexity of devices increases so does the potential for cyber security risk through hardware and software vulnerabilities and increased exposure to network and internet-based threats.
In order to support Australia's medical device cyber security capability, the TGA has produced cyber security guidance for industry as well as guidance for users to embed cyber security practices and protocols across the medical device sector (developers, manufacturers, sponsors, health professionals and patients).
Note
TGA requirements may not be the only relevant regulatory requirements. For example, you might be required to use the Office of the Australian Information Commissioner's Notifiable Data Breach Scheme under the Privacy Act 1988.
Manufacturer and sponsor responsibilities
Manufacturers and sponsors need to consider and plan for an evolving cyber security landscape in order to maintain patient safety.
The cyber–physical–human nature of many connected medical devices leads to cyber security vulnerabilities that cover traditional information security challenges, but also physical patient safety, though these are by nature difficult to predict.
For example:
- Infusion pumps wirelessly connected to a number of systems and networks, introduce many cyber security vulnerabilities and threats, such as unauthorised access to health information and changes to the functionality of the device and prescription of drug doses.
- Digitalisation is blurring the distinction between medical devices and consumer devices, with smartphones able to act as the operating platform for some software-based medical devices. Security of these devices relies on the user, often a patient, having up to date security software on their device and following cyber safe practices.
Enabling medical devices to be cyber-secure is a requirement for regulatory compliance in Australia.
Supporting greater cyber-maturity and resilience into Australia's medical device industry will improve the security culture of our healthcare industry and reduce the risk of devices causing patient harm through cyber vulnerabilities.
To achieve this, medical device manufacturers and sponsors are also considering cyber security more broadly within their organisations, including workforce skills, strong leadership, and technology solutions.
Motivations for malicious activity
Beyond immediate patient harm, a single high profile adverse cyber event can disrupt professional and social trust in medical device advancement and the healthcare system more broadly, hindering innovation, development and deployment of digital health solutions for several years.
Motivations for attacks on medical devices and associated networks may include:
- Financial and political gain through access to identity, financial and medical data stored in hospital IT systems or networks associated with medical devices, through selling of data, blackmail, etc.
- Generating wide-scale disruption of services by gaining entry into hospital networks
- Alteration or removal of a medical service or therapy to impact lives as a form of cyberwarfare, or to target an individual
- Intellectual Property theft
- Impugning the reputation of a device manufacturer in order to alter market competition
- A motivation to harm other individuals
- Curiosity and prestige in demonstrating ability to identify and/or exploit vulnerabilities in complex systems.
Industry trends and cyber security considerations
Highlighted below are emerging social and technological trends that are affecting the cyber threat landscape and associated implications for the healthcare and medical device industry.
The cyber security effect that arises from each trend is an important consideration for all stakeholders in the healthcare and medical device industry.
| Trend name | Trend observations | Cyber security considerations |
|---|---|---|
| Consumer control and experience |
|
|
| Integration of health service and supply chains |
|
|
| Global Connectivity |
|
|
| Large-Scale Device Networking |
Although Bluetooth technology can help the healthcare facilities to improve operational efficiencies it can pose cybersecurity vulnerabilities |
|
| Precision and personal healthcare |
|
|
| Increased data generation and exchange |
|
|
| Healthcare: a vulnerable industry |
|
|
Appendix 3: Frameworks and standards related to cyber security from other sectors
The rapid change of pace of the cyber security threat landscape relative to the development and implementation of standards means that manufacturers, sponsors and in some circumstances, users of medical devices, must continually assess and understand emerging global cyber security standards and frameworks that are being applied across other industries. This might include defence and financial services where infrastructure security and information confidentiality and integrity are primary drivers. It may also include the Internet of Things community within which connected medical devices are implicitly included, especially consumer devices.
The tables below provide a non-exhaustive selection of frameworks and standards that may be of interest to medical device manufacturers and sponsors seeking to include a device in the ARTG in Australia.
Internet of things (IoT)
| Organisation, year | Name of document | Summary |
|---|---|---|
| European Union Agency for Network and Information Security (ENISA) | Baseline Security Recommendations for IoT, in the context of critical information infrastructures | This focuses on security considerations rather than standards. |
| IEEE Standards Association | Internet of Things Related Standards Medical device communications | A comprehensive list of IoT standards Protocols for information exchange |
| National Institute of Standards and Technology (NIST), U.S. Department of Commerce, 2018 | Interagency Report on Status of International Cybersecurity Standardization for the Internet of Things (IoT) (NISTIR 8200) | Covers connected vehicles, consumer IoT, Health IoT, smart buildings, smart manufacturing Looks at cybersecurity risks as well as standards |
Industrial control systems (ICS)
| Organisation, year | Name of document | Summary |
|---|---|---|
| ISA/IEC-62443 series of standards | Industrial Automation and Control Systems Security | Define procedures for implementing electronically secure manufacturing and control systems and security practices and assessing electronic security performance |
| NIST, 2015 | NIST Special Publication 800-82: Guide to Industrial Control Systems (ICS) Security | Guidance on how to secure ICS, including Supervisory Control and Data Acquisition (SCADA) systems, Distributed Control Systems (DCS), and other control system configurations such as Programmable Logic Controllers (PLC), while addressing their unique performance, reliability, and safety requirements. |
| Industrial Control Systems Cyber Emergency Response Team (ICS-CERT), 2016 | Recommended Practice: Improving Industrial Control System Cybersecurity with Defense-in-Depth Strategies | Strategies for defence and recommendations for securing ICS |
Financial services
| Organisation, year | Name of document | Summary |
|---|---|---|
| World Bank Group, 2017 | Financial Sector's Cybersecurity: A regulatory Digest | A compilation of recent cybersecurity laws, regulations, guidelines and other significant documents on cybersecurity for the financial sector. |
Defence
| Organisation, year | Name of document | Summary |
|---|---|---|
| Defence Federal Acquisition Regulation Supplement (DFARS) | Defence Federal Acquisition Regulation Supplements (DFARDS) and Procedures, Guidance and Information (PGI) | DFARS outlines cybersecurity standards a third-party must meet and comply with prior to doing business with the Department of Defence in order to protect sensitive defence information. |
Appendix 4: International guidance on medical device cyber security
We aim to harmonise where appropriate with relevant international guidance.
Many international jurisdictions will have regulatory guidance and information that is in line with global best practice concerning cyber security quality management and risk management systems, and therefore broadly in line with the expectations of the Essential Principles.
Ideally, this facilitates the import and export of medical devices to and from Australia.
There are a number of guidance documents on the cyber security of medical devices that have been published or are under development by international medical device regulators.
Some of these are discussed below. This is not an exhaustive list of global guidance materials. Meeting the regulatory requirements of one jurisdiction does not automatically mean compliance with the Essential Principles.
For a medical device to comply with the Essential Principles, we require that the design and construction will conform with generally acknowledged state of the art safety principles, including quality management and risk management systems.
USA guidance
In the USA, the FDA's Centre for Devices and Radiological Health (CDRH) has published several guidance documents that are relevant for cyber security.
These are available on the FDA website:
- Content of Premarket Submissions for Management of Cybersecurity in Medical Devices
- Post-market Management of Cybersecurity in Medical Devices
- Guidance for the Content of Premarket Submissions for Software Contained in Medical Devices
- Cybersecurity for Networked Medical Devices Containing Off-the-Shelf Software
- Medical Device Data Systems, Medical Image Storage Devices, and Medical Image Communications Devices
Also in the USA, the National Institute of Standards and Technology (NIST), through its National Cybersecurity Centre of Excellence (NCCoE) has produced Cyber Security Practice Guides for various industries, including healthcare:
The ECRI Institute, an independent non-profit organisation that researches approaches to improving patient care, has significant global activity in medical device cyber security and has published a series of relevant subscription based guidance documents (log in required):
- Cybersecurity Risk Assessment for Medical Devices
- Cyber Threats Top ECRI Institute's 2019 Health Technology Hazards
- Cybersecurity: The Essentials
- Anti-Malware Software and Medical Devices: A Crash Course in Protecting Your Devices from Cyber Attacks
- Ransomware Attacks: How to Protect Your Medical Device Systems.
IMDRF guidance
The International Medical Device Regulators Forum (IMDRF) has worked to further a unanimous understanding of challenging topic areas, such as Software as a Medical Device (SaMD), which have a high risk of being exposed to malicious cyber activity.
In addition, IMDRF has recently formed a working group to directly address cyber security.
Relevant documents are available on the IMDRF website (in both PDF and DOCX formats), and include:
- Software as a Medical Device (SaMD): Key Definitions
- Software as a Medical Device (SaMD): Possible Framework for Risk Categorization and Corresponding Considerations
- Software as a Medical Device (SaMD): Application of Quality Management System
- Software as a Medical Device (SaMD): Clinical Evaluation.
European guidance
In Europe, the new Medical Device Regulation has introduced a specific requirement for cyber security for medical devices. This Regulation, (EU) 2017/745, will be fully implemented by 2020.
More broadly, the European Union Agency for Network and Information Security (ENISA) has published guidance on baseline security for Internet of Things (IoT) Baseline security recommendations for IoT in the context of critical information infrastructures
Other jurisdictions
Cyber security for medical devices is a growing area of focus across many other jurisdictions. In some of these jurisdictions, authorities external to country's health departments are investigating cyber security approaches for a range of Internet of Things devices, including connected medical devices.
Examples of guidance are highlighted below.
Note that some of these are draft, and the fast-moving nature of this topic means that there are many jurisdictions and examples of guidance not included here:
- South Korea's Ministry of Science and ICT together with the Korea Internet and Security Agency (KISA) released a Cyber Security Guide for Smart Medical Service' which aims to address security threats that may arise in smart medical services and how to respond to them.
- The Singapore Standards Council technical reference on Connected medical device security
- Health Canada's draft guidance document on the Pre-market requirements for medical device cyber security.
Glossary
The glossary for this guidance is included in the TGA glossary.
Footnotes
- See Division 1 of Part 4-11 of Chapter 4 of the Therapeutic Goods Act 1989.
- The revised Essential Principle 12.1 came into effect on 25 February 2021. Its represents the TGA’s current expectations regarding cyber security for devices of this type.
- Software Assurance Forum for Excellence in Code (SAFECode), Fundamental Practices for Secure Software Development; Essential Elements of a Secure Development Lifecycle Program, Third Edition, March 2018, [Online] Available from: https://safecode.org/wp-content/uploads/2018/03/SAFECode_Fundamental_Pr… (pdf,762kb)* - Accessed: 10/03/19
- Therapeutic Goods (Medical Devices) Regulations 2002, Schedule 1, clause 2(1) - Essential Principle 2(1)
- Speer, J. (n.d.). The definitive guide to ISO 14971 risk management for medical devices, [Online] Available from: https://www.greenlight.guru/hubfs/Sales_Material/gg_guide_to_risk_manag… (pdf,339kb). Accessed: 9/11/2018
- NIST (2018). Framework for Improving Critical Infrastructure Cybersecurity, [Online] Available from: https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf (pdf,1.01Mb)*. Accessed: 28/09/2018
- Essential Principle 9.2(b)
- Storm, B., Battaglia, J., Kemmerer, M., et al (2017). Finding Cyber Threats with ATT&CK™-Based Analytics, MITRE Corporation, [Online] Available from: https://www.mitre.org/sites/default/files/publications/16-3713-finding-… (pdf,710kb)* Accessed: 13/03/2019
- See subsection 41FN(3) of the Therapeutic Goods Act 1989
- See Part 4-6 of Chapter 4 of the Therapeutic Goods Act 1989
- See subsections 41MN(1), (4) and (4A) of the Therapeutic Goods Act 1989
- See subsection 41MNA(1)) of the Therapeutic Goods Act 1989
- Potential harm to a patient from the exploitation of a cyber security vulnerability may include physical or psychological harm through negative impact on the patient's health and safety. Other risks may be privacy or financial.
Page history
Changes to align with the Procedure for Recalls, Product Alerts and Product Corrections (PRAC) which replaced the Uniform Recall Procedure for Therapeutic Goods (URPTG) from 5 March 2025.
Title changed from 'Medical device cyber security guidance for industry' to 'Complying with medical device cyber security requirements' as part of migration to new 'Guidance' content type:
- Consistent ‘Purpose’ heading.
- ‘Legislation’ section to clearly show which laws the Guidance relates to.
- ‘Page history’ section replaces document version history.
- New page navigation features.
- Updated page summaries.
- Complex images include long descriptions.
- New ‘Save as PDF’ feature.
Changes to further align with the Australian Cyber Security Centre.
Additional advice on revised Essential Principles.
Original publication.
Changes to align with the Procedure for Recalls, Product Alerts and Product Corrections (PRAC) which replaced the Uniform Recall Procedure for Therapeutic Goods (URPTG) from 5 March 2025.
Title changed from 'Medical device cyber security guidance for industry' to 'Complying with medical device cyber security requirements' as part of migration to new 'Guidance' content type:
- Consistent ‘Purpose’ heading.
- ‘Legislation’ section to clearly show which laws the Guidance relates to.
- ‘Page history’ section replaces document version history.
- New page navigation features.
- Updated page summaries.
- Complex images include long descriptions.
- New ‘Save as PDF’ feature.
Changes to further align with the Australian Cyber Security Centre.
Additional advice on revised Essential Principles.
Original publication.

